Tracing the Trail of the Upbit Hack
Blockchain forensics of the Upbit hack. We traced how the Upbit hackers concealed the origin of funds and cash out stolen ETH through exchanges.
Cylynx
May 27, 2020 · 4 min read
Blockchain forensics of the Upbit hack. We traced how the Upbit hackers concealed the origin of funds and cash out stolen ETH through exchanges.
Cylynx
May 27, 2020 · 4 min read
On 27 November 2019, hackers made off with 342,000 Ethers (ETH), close to $45 million at that point of time, stolen from Upbit, a South-Korean based cryptocurrency exchange in a single transaction. This was subsequently confirmed by the CEO of Upbit in a press release later in the afternoon.
I am Seok-Woo Lee, CEO of Dumu who runs Upbit.
First of all, we apologize for any inconvenience caused by the members who use Upbit.
On November 27, 2019, at 1:06 PM, up to Ethereum Hot Wallet, 342,000 ETH (approximately 58 billion won) were transferred to the unknown wallet.
The address of the unknown wallet is 0xa09871AEadF4994Ca12f5c0b6056BBd1d343c029.
A few days later, the hacker moved a large amount of ETH to other wallets in an attempt to obscure the origin of funds. This was covered by major cryptocurrency news websites such as Coindesk and Cointelegraph.
Since then, numerous regulators have launched investigations into the hack. An indictment charge brought about by The United States Justice Department’s Criminal Division has implicated two Chinese nationals in the hack and uncovered a larger case of money laundering and collusion with North Korean hackers:
The pleadings further allege that the North Korean co-conspirators are tied to the theft of approximately $48.5 million worth of virtual currency from a South Korea-based virtual currency exchange in November 2019.
According to the Department of Justice press release, 113 cryptocurrency accounts and addresses (both in Bitcoin and Ethereum) were involved in the hack and money laundering trail.
The civil forfeiture complaint specifically names 113 virtual currency accounts and addresses that were used by the defendants and unnamed co-conspirators to launder funds. The forfeiture complaint seeks to recover the funds, a portion of which has already been seized.
Leveraging our tracing algorithm documented in the previous blog post, we analyzed the activities post-hack and found sustained efforts to obscure the origin of funds spanning 50k Ethereum wallets and 100k transactions. Despite the indictment charges, activities surrounding the wallets involved in the Upbit hack still remain high and might have even rebounded.
Based on the address information made available by Upbit’s press release we are able to trace the subsequent movement of funds.
Etherscan captures the initial movement of funds 342,000 ETH from Upbit3 to the hacker wallet at block 9007863, transaction hash 0xca4e0aa223e3190ab477efb25617eff3a42af7bdb29cdb7dc9e7935ea88626b4.
The next day most of the hacked Ethers were moved to three wallets tagged as Upbit Hacker 2.1 and Upbit Hacker 2.2 and Upbit Hacker 2.3.
This peeling chain of transactions continued until early January. For example, Upbit Hacker 2.1 moved funds to Upbit Hacker 3.1 and Upbit Hacker 3.2 which further subdivided the funds into other wallets. Etherscan has 815 accounts and 1374 transactions tagged as being closely associated with the Upbit hack, some of these ending up in exchanges - probably an indication that the hackers were trying to cash out ETH for fiat currency.
Our tracing technology allows us to identify all funds that originated from the hacked wallet. This helps us to expedite the investigation process and automatically tag suspicious wallets.
An automated approach to transaction monitoring allows us to keep track of all the wallets involved in the movement of hacked funds. For each transaction, we estimated the amount of ether associated with the Upbit hack by calculating the proportion of funds that could be traced back to the hacker’s account.
A sample flow of funds from the original hacked account (Blue) to the Binance Exchange can be seen in the figure below. Funds are often spread out to multiple accounts before converging back to be cashed out. Attempts to obfuscate the transaction trail by sending ETH between various hack wallets can also be observed.
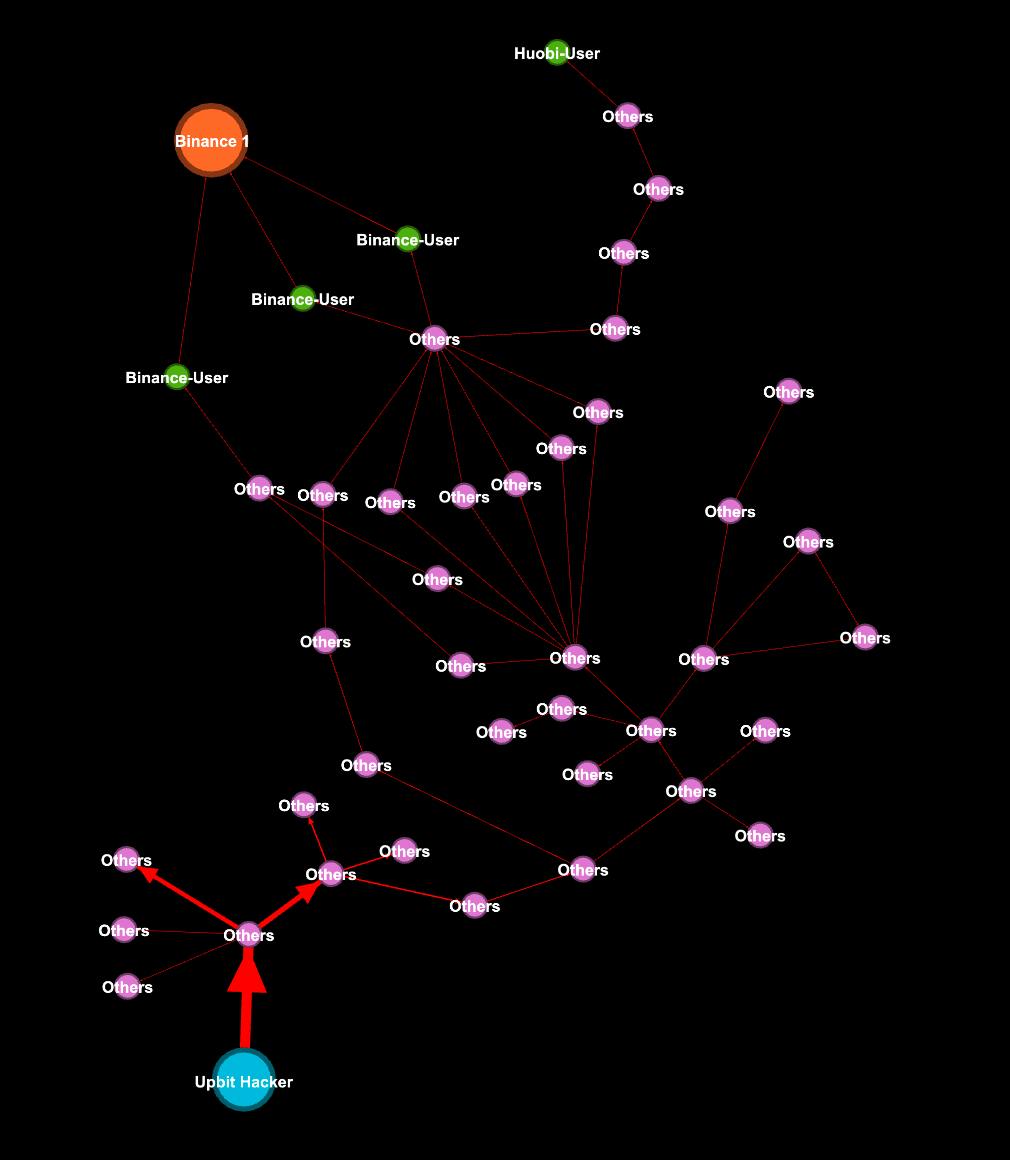
Not surprisingly, a large amount of hack funds finds its way to exchanges as hackers are looking for avenues to wash the funds.
Hackers are trying to elude regulatory checks by taking advantage of the pseudo-anonymity and ease of creating new wallets offered by the blockchain to create transaction trails that would obscure the true sources of funds.
The animated transaction trail shows how funds are transferred between numerous intermediate wallets before finding their way to the big centralized exchanges. We focused only on transactions which contains more than 85% of Upbit funds.
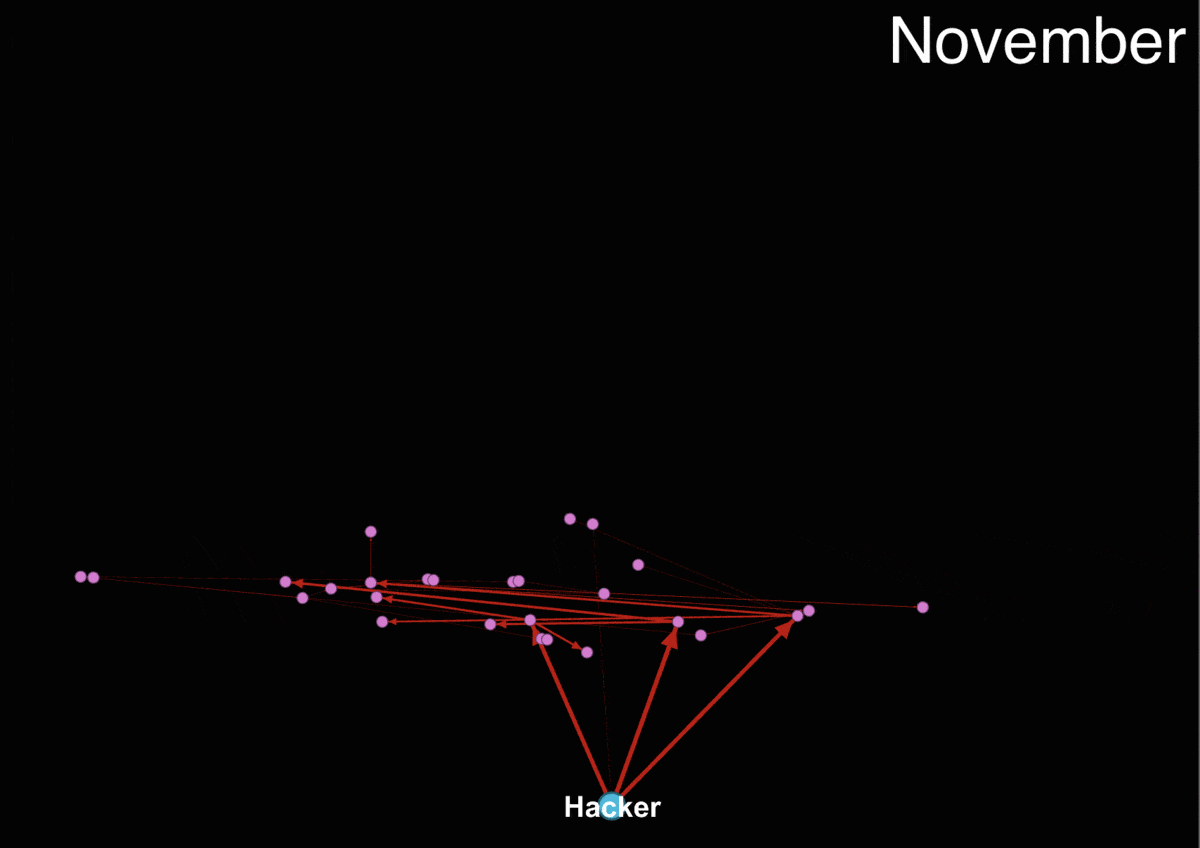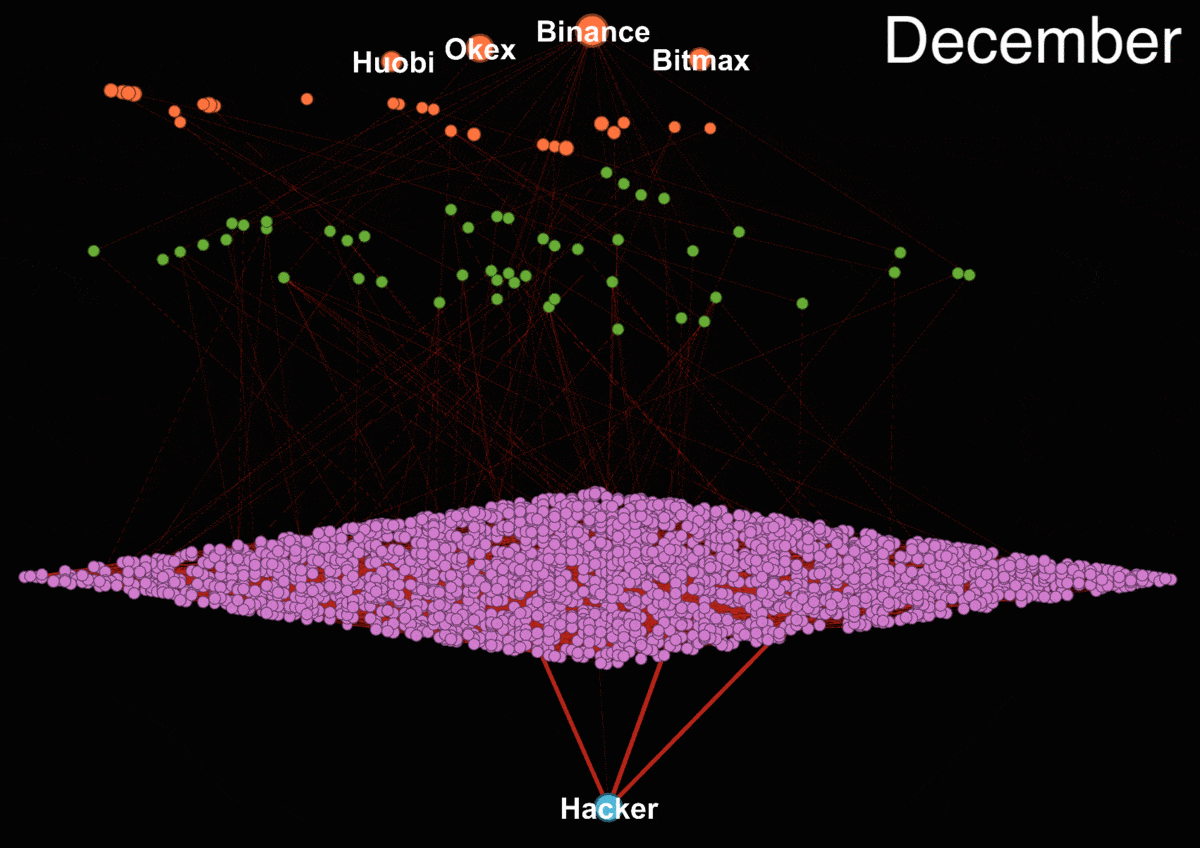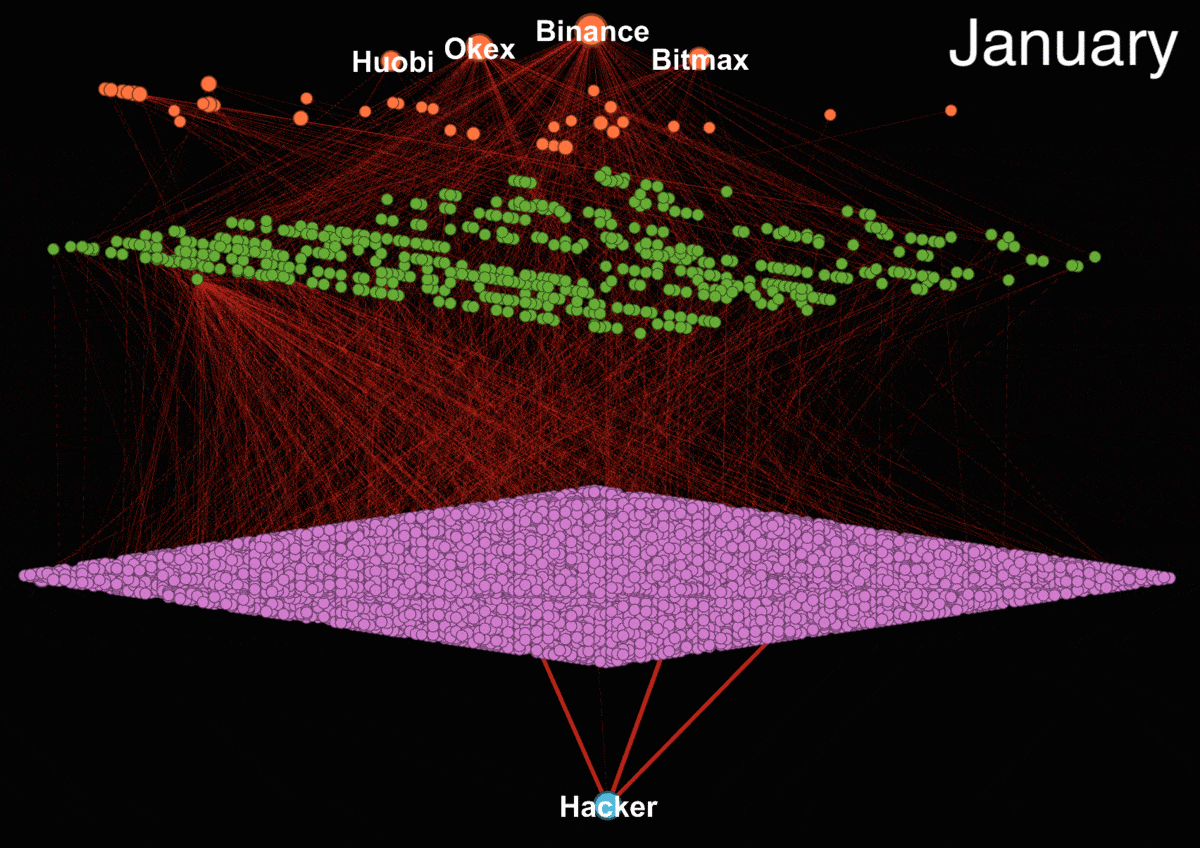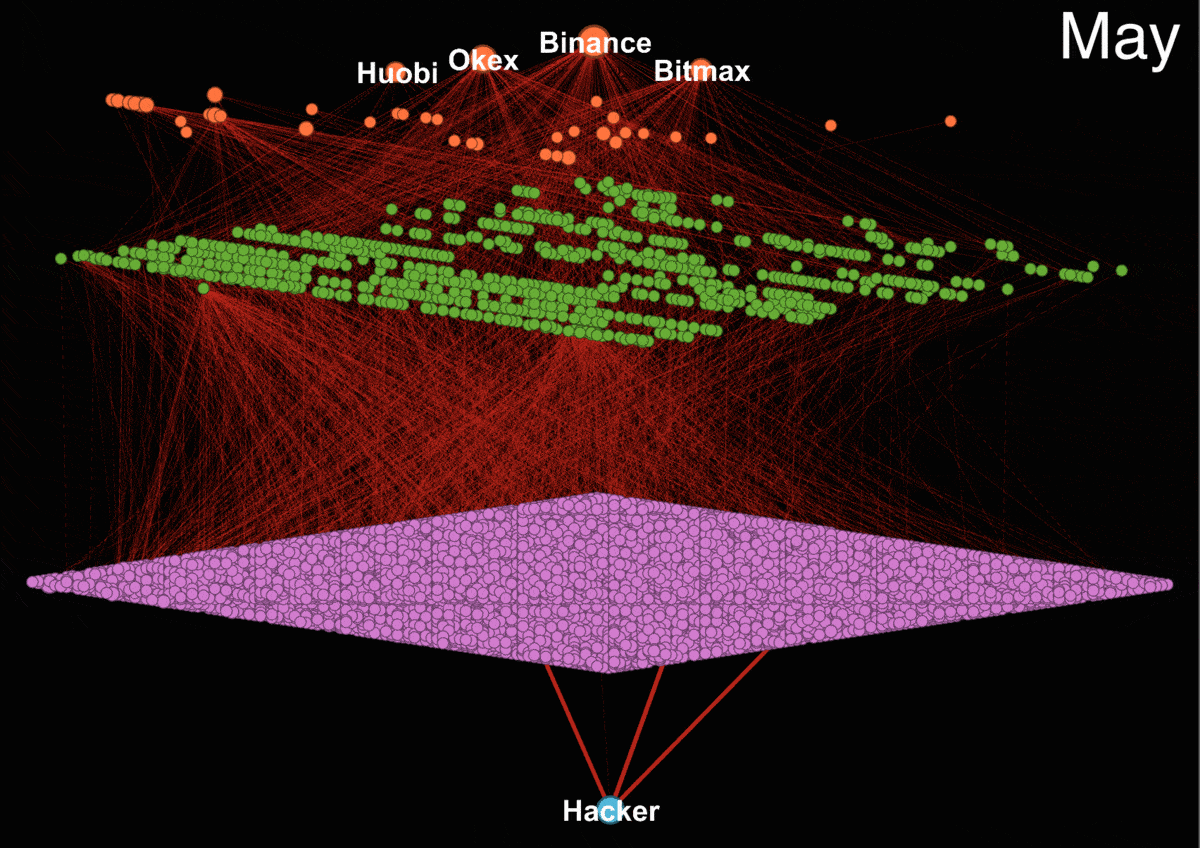
Our analysis shows that the hackers are trying to cash out primarily through four exchanges - Binance, Huobi, Okex, and Bitmax. It is impossible to tell from the blockchain data whether they were successful in doing so since the exchanges could be working with regulators and holding the funds. In fact, evidence from the Department of Justice report and tweets from Binance CEO Zhao Changpeng suggest that exchanges are working proactively to freeze the associated funds.
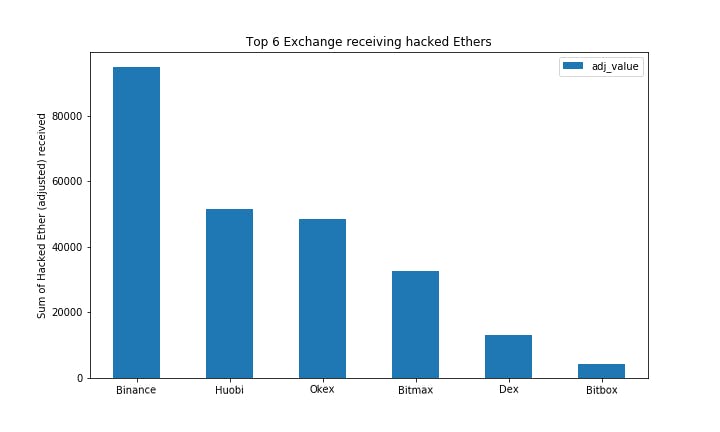
Prior to May, we calculated that approximately 190,000 - 240,000 of hacked ETH have reached various Exchange addresses, where they were either unknowingly cashed out or possibly frozen by the exchanges.
A plot of the movement of hacked funds across time is shown below:
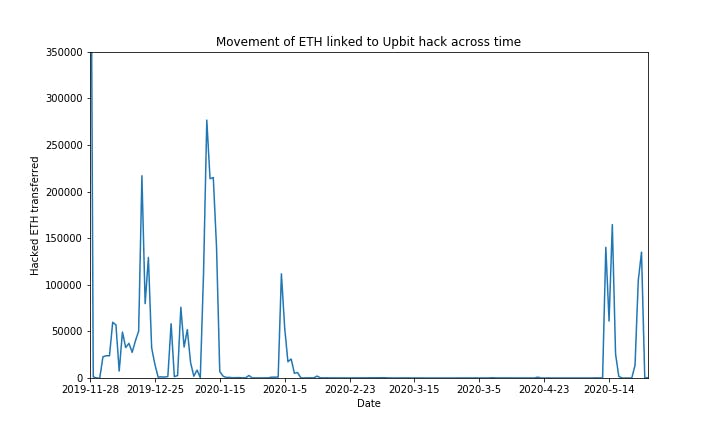
A resurgence of activity was seen in May with attempts to cash out the hacked funds.
In the past three weeks, approximately 65,000 - 75,000 of hacked ETH was moved to various exchange entities. Approximately, 25,000 - 85,000 of ETH remains held in multiple untagged wallets e.g. 0x1543383478ee006599a41b19a991b46ebfc37ed4
This article highlights the sophisticated methods used by the Upbit hackers to launder stolen money, with exchanges playing a key role in the ecosystem, being the eventual destination for these hacked funds.
While Know Your Customer (KYC) solutions are popular in the industry for regulatory compliance, they only provide a basic check at the point of application and should be supplemented by more robust tools.
Regulators and compliance teams should take full advantage of the transparency offered by the blockchain. A transaction monitoring platform such as what Cylynx offers aims to provide a more holistic risk assessment by aggregating information across all blockchain transactions. Contact us if you are interested in trying out our platform or want custom tracing of transaction trails.